I “wannacry” (couldn’t help it) when I think about the proliferation of the recent ransomware attack that affected over 200,000 systems in over 100 countries. Ruthlessly, this malware brought down rail and hospital systems alike. This is where it gets “real” and forces organizations of any size to evaluate their ability to mitigate such invasive and life-threatening attacks.
Back to Basics
Who or where can we turn towards to get help on reducing exposure to such threats? One such place is the “Center for Internet Security” which is a nonprofit entity that harnesses the power of a global IT community to safeguard private and public organizations against cyber threats. CIS publishes a set of guidelines, called the Critical Security Controls, which lists 20 critical things organizations should implement to defend against modern cyber threats. Below is a graphic of the controls prescribed by the CIS and its global IT community.
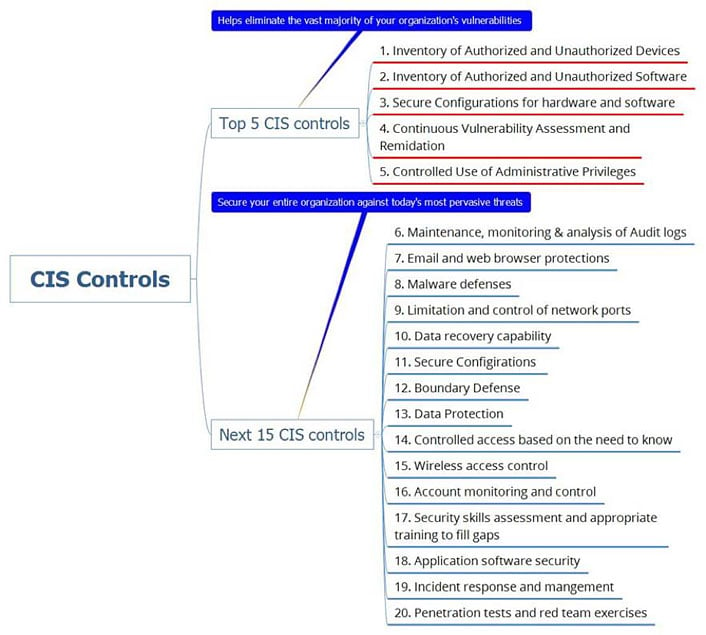
Controls that Would Have had a Significant Impact
Although this article is not a comprehensive look at all of these security controls, it is intended to illustrate how some of these controls could have helped reduce the number of infected systems due to the recent WannaCry ransomware attack.
- Control #3: focuses on actively managing security controls on laptops, servers, and workstations via configuration and change management programs. This is directly applicable to the WannaCry attack as the malware wormed its way into systems without current security patches installed on Windows hosts.
- Control #4: provides an organization the ability to assess their systems and posture for known vulnerabilities. If implemented correctly, mis-configurations and missing patches could have been identified before the malware hit.
- Control #8: Modern malware is designed to hide from defenses and the attack vectors are continually evolving. Implementing malware detection and prevention systems at appropriate boundries could have prevented infection in some cases and limited the spread in others.
- Control #9: Modern attackers are extremely sophisticated and constantly updating their attack plans. For this reason it is important to make sure services, ports and protocols are not used superfluously and are exposed only when necessary.
- Control #10: Once the malware takes hold and files are encrypted, a backup may be the only option available to recover your data. For this reason, backups and recovery capabilities are paramount.
These are just some of the controls that could have reduced the impact on the latest and noteworthy ransomware attack.
Where to Start
If you are uncertain of your security posture, a great place to start is to review all 20 of these controls for applicability in your environment. More than likely, you will need them but don't get overwhelmed by what you do or don't have in place. You can always turn to a qualified partner, such as Solutions II. Solutions II's security experts can help you navigate through these controls and strengthen your defenses. Check out Solutions II's Security Solutions or contact us at
info@Solutions-ii.com.




Comment Form