Security Controls generate so much data and noise that they ultimately break at scale while correlating the data, performing data analysis, researching threat data, and then trying to take relevant action on EVERY alert generated. Additionally, this layered approach, along with the distributed nature of an organization’s assets, increased risk caused by factors such as:
The first evolutionary step of a maturing security operation was a Security Incident and Event Management (SIEM) platform. These tools all vary in capabilities; however, common to all SIEM platforms are:
Once an alert is generated from the SIEM, a Security Analyst must perform additional work (further investigation, determination of event nature (true/false), tuning, and/or response) that is part of security operations.
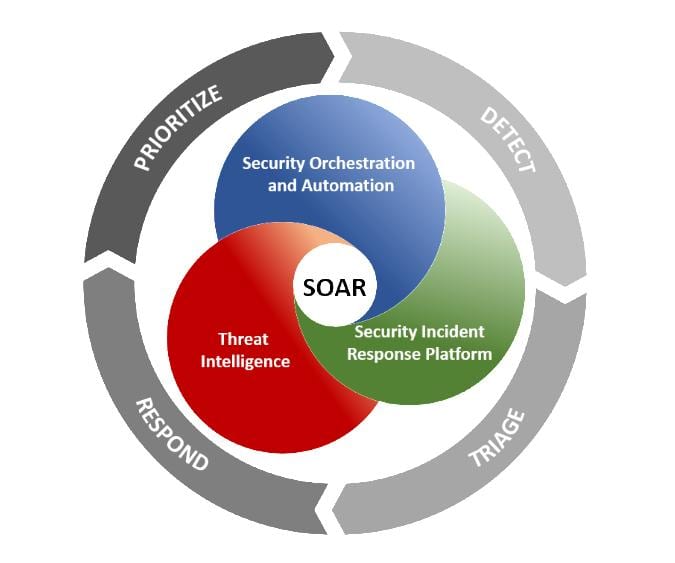
The next evolution step in Security Operations maturity came in the way of Security Orchestration and Automated Response (SOAR) platforms and tools. These platforms allowed the security operations team to build out repeatable automated response capabilities that included orchestrating specific actions on various security controls when specific security events occur. Organizations that have a mature security program with documented processes and procedures for enriching security investigations with the data available from their security controls as well as playbooks for response, SOAR platforms can be a force multiplier for security operation teams. Additionally, these platforms create efficient, consistent, and auditable response capabilities.
Endpoint security has evolved from legacy antivirus using signature-based detection methods to what’s known as Endpoint Detect and Response (EDR) tools. EDR tools monitor and analyze ALL events and operations on an endpoint. Many of these modern platforms use some form of AI or Machine Learning to monitor activity and perform behavior analytics to prevent security incidents before they occur. Additionally, the Response capability in these EDR tools allows for a security operations team to act, such as isolating an endpoint on the network if malicious activity is observed, allowing the security operations team to prevent the lateral spread of an attack.
EDR platforms typically generate quite a bit of data since they monitor ALL compute operations on every endpoint in the organization regardless of whether the endpoint is on or off-network. While EDR tools are incredibly powerful at detecting and potentially stopping an attack with their response capabilities, this is only realized when you have the resources to monitor and respond, requiring “eyes on glass” at all times to intervene and respond as needed. This requirement has created Managed Detect and Response (MDR) services. An MDR service can monitor your EDR platform 24/7 and initiate action on events in near real-time, preventing the lateral spread of an attack or, in some cases, prevent an actual security incident from ever occurring. In most cases, a robust EDR platform combined with an MDR service has a better ROI than most security controls combined due to detecting security events early and enabling response capabilities to stop an attacker.
With all the security controls and security services combined, organizations are still at risk of security incidents. The impact of a security incident completely varies based on the type of threat and the “dwell” time that the attacker has within your organization before detection and response. When a security incident does occur, detecting the incident and responding on the incident EARLY is key. A security Incident Response plan carried out by knowledgeable experienced incident responders can be the key to reducing the impact of the incident as well as reducing the recovery time for business operations. While there are many types of cyber threats that pose a risk to your organization, ransomware continues to be one of the most painful for most organizations. If your organization is impacted by ransomware or another cyber threat, you may want to consider having a retainer for an Incident Response team such that contracts will already be in place, cost will have already been negotiated, and engagement methods will be determined. This gives your organization the assistance it needs to stop and isolate attacks, perform forensics to determine the root cause or point of entry, collect evidence (if needed) for law enforcement and/or regulatory needs, and ultimately get your organization operational again.
If your organization is struggling with analyzing, operationalizing, and responding to security events, let us know. Solutions II can help evaluate your security program, review your security architecture, and help operationalize your security response. This may include augmenting your organizations security operations team with deployment of SIEM/SOAR technologies, providing MDR services, and/or Incident Response in the case of an active security incident.
We can evaluate your security program, review your security architecture, and help operationalize your security response.
©2024, SOLUTIONS II ALL RIGHTS RESERVED,PRIVACY POLICY