Why regulations, such as GDPR, are valuable to adhere to - even if you are not mandated to follow it.
Definitions*
- The term "privacy" denotes a socially defined ability of an individual (or organization) to determine whether, when, and to whom personal (or organizational) information is to be released.
- The term "security" describes techniques that control who may use or modify the computer or the information contained in it.
- The General Data Protection Regulation (GDPR) (Regulation (EU) 2016/679) is a regulation by which the European Parliament, the Council of the European Union and the European Commission intend to strengthen and unify data protection for all individuals within the European Union (EU). It also addresses the export of personal data outside the EU. The primary objectives of the GDPR are to give control back to citizens and residents over their personal data and to simplify the regulatory environment for international business by unifying the regulation within the EU. When the GDPR takes effect, it will replace the data protection directive (officially Directive 95/46/EC) from 1995. The regulation was adopted on 27 April 2016. It becomes enforceable from 25 May 2018 after a two-year transition period and, unlike a directive, it does not require any enabling legislation to be passed by national governments and is thus directly binding and applicable.**
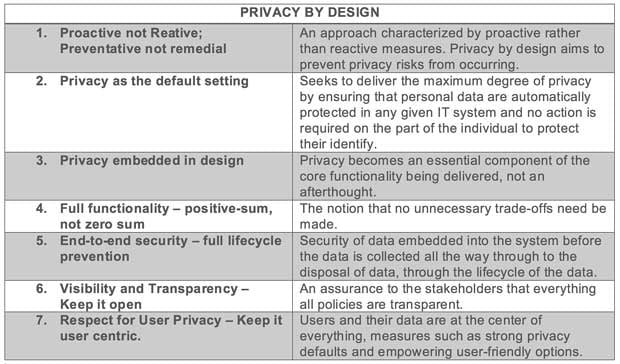
Privacy by Design
Privacy by design (PbD): a framework described by Dr. Ann Cavoukian, promoted the concept while acting as the Information and Privacy commissioner in Ontario, Canada and an advocate of default online privacy. She is currently the Executive Director of the Privacy and Big Data institute at Ryerson University.PbD, a framework that has been around since the 90’s evangelizes a user centric (openness and transparency) approach to privacy, by keeping the user and their data at the center of all things important, theorizes 7 foundational principles to control the effects of information and communication technologies. They are:
Security by Design
Security by design: there are a set of core principles that need to be taken into consideration ahead of a software development life cycle.
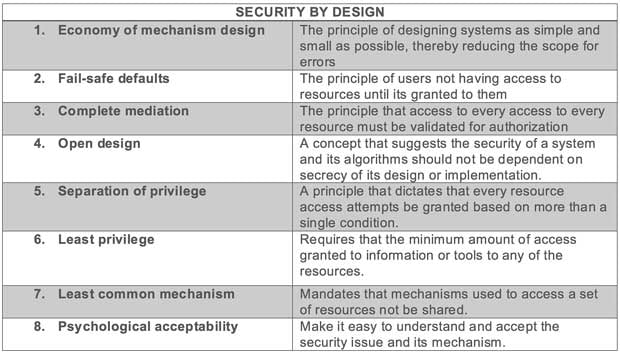
Sources: https://dzone.com/articles/9-software-security-design, http://nob.cs.ucdavis.edu/classes/ecs153-2000-04/design.html
We live in a world where breaches of privacy and security are becoming common place. Unfortunately, this comes as no surprise to anyone. But at the same time, organizations embrace technologies (and rightfully so) that cause us to willingly give up some control of our data and resources (such as cloud computing). Organizations face so much competitive pressure, privacy and security can become an afterthought until such a time a breach has occurred or when a compliance standard is imposed on them.
It is common for organizations to follow a cadence of proactive inspection of the security posture when imposed via compliance and regulatory requirements, in other words forced to do so to avoid penalties and fines. Others focus on it because of a breach or an event having occurred. Finally, there are those that are proactive in nature and seek actively to maintain a current security posture.
The reality is that security compliance regulations standards are a good way of protecting your organization and the privacy of the individuals involved with the organization even if you are not necessarily mandated regulations. It’s just good practice because it promotes adherence to security and privacy guidelines that will expose some of the basic requirements that enable good privacy and security measures.
For example, one of the key activities that would occur while assessing an organization's compliance with the GDPR regulations is discovery and classification of data assets and the systems that control such data. This should be treated as good practice and enabled by default. A big problem that most companies grapple with is the uncontrolled growth of data/storage in the environment and not having any kind of visibility into it. There are estimates that this ROT data (Redundant, Obsolete & Trivial) constitutes somewhere between 70 and 80% of the total data stored in the environment. This undoubtedly has real cost implications to it because historically, the solution was to throw more hardware into the environment once a capacity threshold has been reached. There are also operational and security implications, because if you don’t know what you have, you are likely not to take appropriate security measures.
Regulations such as GDPR (and several others) are good way to gain control over the security posture of your environment as it promotes some of the required design principles and forces organizations to look inwards proactively. For all of your Security/Compliance and GDPR needs, please visit us at www.solutions-ii.com/security!




Comment Form