The best chance of discovering and defeating information exploitation and theft is a disciplined, programmatic approach to discovering and mitigating threats and vulnerabilities. Threat and Vulnerability Management (TVM) is a programmatic approach to reducing risk to critical assets in your organization through a cyclical process that identifies, assesses, classifies, remediates, and mitigates the following controls/processes:
KNOW your hardware and software assets. Hardware Assets include devices like servers, workstations, storage devices, printers, etc. Non-traditional devices also included would be, BYOD, IoT devices and/or devices connected to the network.
Software is also an asset. It can be a standalone application deployed on a single device or a more complex asset comprised of multiple functions and services running on multiple assets.
Discovering, cataloging, classifying, dependency mapping, and reporting are all functions of asset management. Asset management is a critical security control, specifically; CIS Critical Security Control #1 and #2. Managing assets is a key component of a Threat Vulnerability Management program since you must first be knowledgeable of your assets to secure them. Once you have a documented inventory of all hardware and software assets, you can begin the Vulnerability Management stage.
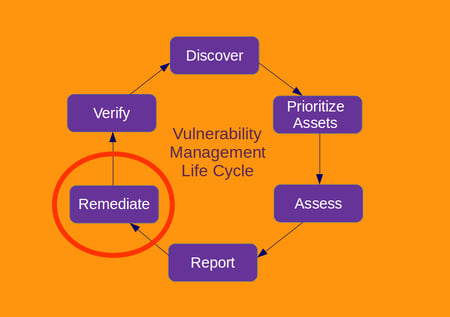 Vulnerability management includes the discovering/scanning of all assets for exposure. This process facilitates asset discovery and is used to update data elements within the asset management component of the process. Vulnerability scanning engines typically have a catalog of known vulnerabilities to compare/correlate scan results. The resulting output shows vulnerabilities in the assets scanned to prioritize, assess, and report. Managing these vulnerabilities is a critical security control, specifically; CIS Critical Security Control #3. Identified vulnerabilities should be prioritized and remediated based on the overall risk to an organization’s critical assets. Remediating these vulnerabilities is typically handled through a Patch and Configuration Management process.
Vulnerability management includes the discovering/scanning of all assets for exposure. This process facilitates asset discovery and is used to update data elements within the asset management component of the process. Vulnerability scanning engines typically have a catalog of known vulnerabilities to compare/correlate scan results. The resulting output shows vulnerabilities in the assets scanned to prioritize, assess, and report. Managing these vulnerabilities is a critical security control, specifically; CIS Critical Security Control #3. Identified vulnerabilities should be prioritized and remediated based on the overall risk to an organization’s critical assets. Remediating these vulnerabilities is typically handled through a Patch and Configuration Management process.
Vulnerabilities in assets are typically remediated through a process of configuration management (uninstalling, disabling, modifying services that are vulnerable on an asset) or by patching the vulnerability with an available software patch. You can also remediate vulnerabilities with host-based IPS controls to block the exposed vulnerability from being accessed. This vulnerability remediation process is time and labor-intensive, and while it might lower risk, it might create additional risk if the changes impact availability. The recommended solution is to create a programmatic approach to remediation based on asset criticality and risk. Once remediation has taken place, the asset management solution should be updated with the appropriate changes.
This entire cyclical process is Threat and Vulnerability Management. This is a process that all organizations should implement to reduce cyber risk and improve security posture. Solutions II can help develop and/or improve your Threat and Vulnerability Management program through solutions and services around all components in this process.
We can help develop and/or improve your Threat and Vulnerability Management program through solutions and services around all components in this process.
©2024, SOLUTIONS II ALL RIGHTS RESERVED,PRIVACY POLICY